Consent options in Microsoft 365 profiles
Overview
What's important to understand first is that there are only 2 options from an application perspective to give consent: Someone has given consent for the Synchronizer to access a certain resource, or there is no consent given.
The consent can either be given by the users themselves or by an Azure administrator using a so-called tenant-wide admin consent.
Also, giving consent does not mean the application can access the resources for which the consent has been given. The user still needs to provide an access token to the application (details below).
How to
Scenario 1: the flow for customers using the default configuration
- A SuperOffice admin user sets up the Nebule Synchronizer
- By pressing the Connect button in the portal we initiate an OAuth flow in Microsoft 365
- Our application will ask for access to a couple of resources so this admin has to give consent to our application to access these resources. This is a personal consent, only giving access to his/her own resources
- This will also automatically register the app in the customers Azure Active Directory
- When the admin links regular users we need to request access to the calendar of each link user
- The regular user will receive an email, clicks on the link and is also redirected to Microsoft 365 to start the OAuth flow
- We will ask them to give consent to access their calendar (because the admin only gave consent for his own account)
- After the user gives consent to receive a token with which we can access the resources the user has given consent for.
Scenario 2: Customer that does not want regular users to give consent to Microsoft 365 applications. Bypass User Consent option
Since we have more and more enterprise customers we also needed to handle a new scenario: a customer that does not want regular users to give consent to Microsoft 365 applications. In this scenario, an Azure Active Directory Admin needs to give consent for all users in the Azure tenant and the Synchronizer does not need to ask for this consent anymore. For your convenience we have put 4 screenshots below how to acomplanish this.
The flow looks like this:
- A SuperOffice admin user sets up the Nebule Synchronizer
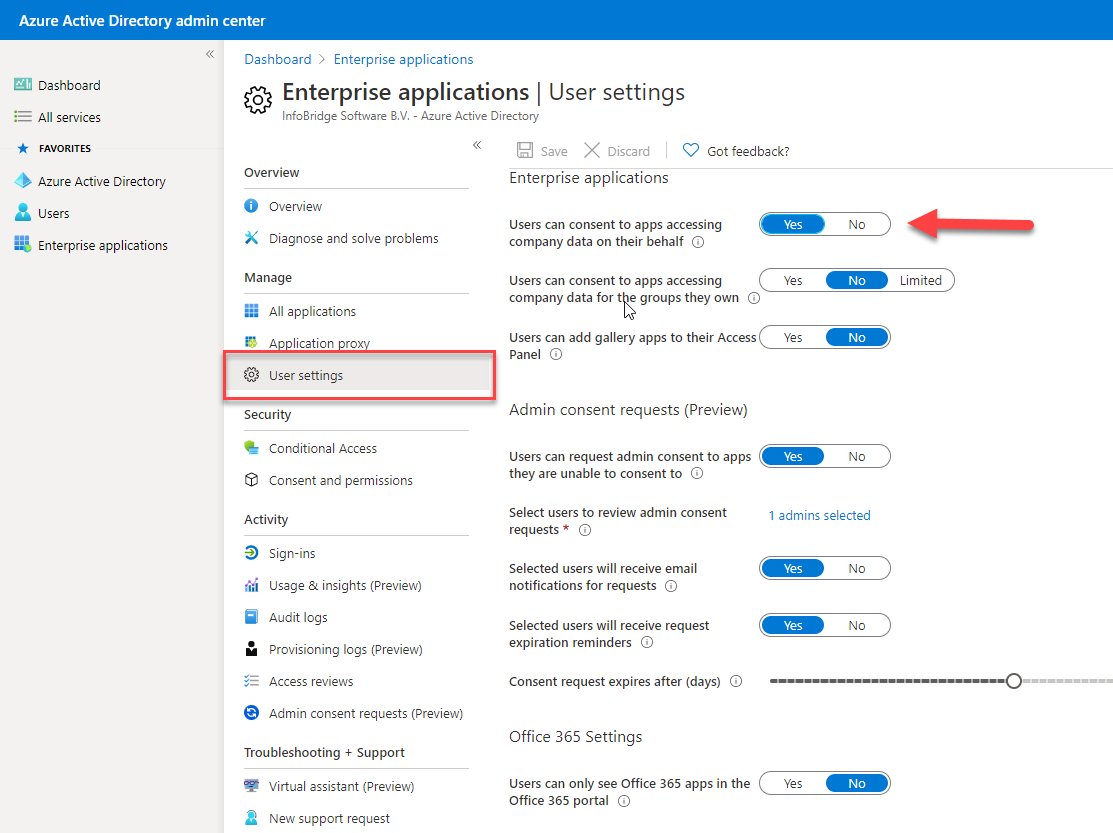
- The option: by-pass user consent is enabled, see screenshot below
- By pressing the connect button in the portal we initiate an OAuth flow in Microsoft 365
- Our application will only ask the SuperOffice admin user to login and no longer asks for consents
- When the admin links regular users we still need to request access to the calendar of each link user
- The regular user will receive an email, clicks on the links and is also redirected to Microsoft 365 to start the OAuth flow
- We will ask the user to login to Microsoft 365
- After the user logs in, we receive a token with which we can access the resources the Microsoft 365 have given consent for.
From a technical perspective, the only thing that "by-pass user consent" does, is removing "&prompt=consent" from the URL that we redirect the user to, to log in:
Note on the Azure option "User can consent to apps accessing company data on their behalf"Users can consent the synchronizer app to access data. It is usually not allowed by organizations, only azure admins are allowed to consent to access data, but when creating a profile in the sync we need permissions. So Either the azure admin should create a profile and accept the permissions or allow users to consent |